
Articolo originale di Dominik Zajacpubblicato sul suo blog
Al tempo delle connessioni wifi gratuite e connessioni internet gratuite in ogni bar, o caffè si dovrebbe essere sicuri che i propri collegamenti siano sicuri. In alcuni casi non è possibile fidarsi della connessione, ma è necessario andare online e leggere alcune mail o condividere alcuni documenti. In questi casi alcuni strumenti di base come SSH e Firefox possono aiutare a costruire una connessione sicura ad un computer conosciuto in internet di cui ci si può fidare (per esempio il proprio server stesso).
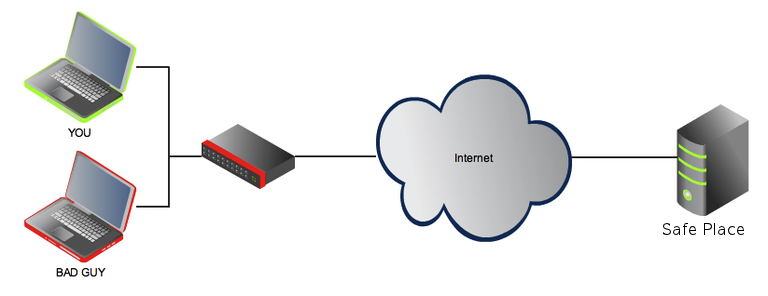
Per rendere più chiaro ciò di cui sto parlando ho creato questo piccolo diagramma per rendere più facile per me spiegare quello che sto facendo con questa connessione SSH e come posso trarre beneficio da essa.
Diciamo che mi sono connesso con una rete pubblica o access point wifi. Ci sono molte persone intorno a me che stanno usando la stessa connessione ed io non conosco il fornitore della rete molto. Una cosa che posso fare per ottenere una connessione sicura è quella di aprire un tunnel SSH alla mia macchina conosciuta e inviare tutto il traffico che genero con il mio browser web attraverso questo tunnel.
Questo può essere fatto con un comando SSH come questo:
ssh -D 8080 username@host |
Che cosa fa questo comando è spiegato nelle pagine man del comando ssh:
-D [bind_address:]port Specifies a local “dynamic” application-level port forwarding. This works by allocating a socket to listen to port on the local side, optionally bound to the specified bind_address. Whenever a connection is made to this port, the connection is forwarded over the secure chan- nel, and the application protocol is then used to determine where to connect to from the remote machine. Currently the SOCKS4 and SOCKS5 protocols are supported, and ssh will act as a SOCKS server. Only root can forward privileged ports. Dynamic port forwardings can also be speci- fied in the configuration file. IPv6 addresses can be specified with an alternative syntax: [bind_address/]port or by enclosing the address in square brackets. Only the superuser can forward privileged ports. By default, the local port is bound in accordance with the GatewayPorts setting. However, an explicit bind_address may be used to bind the connection to a specific address. The bind_address of “localhost” indicates that the listening port be bound for local use only, while an empty address or `*’ indicates that the port should be available from all interfaces. |
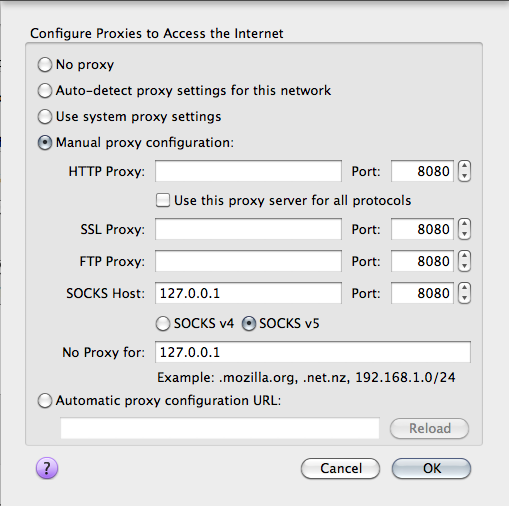
Ora ho una porta locale (8080) attraverso la quale posso inviare il mio traffico. La sola cosa che devo fare ora è quella di riconfigurare il mio Firefox per utilizzare questa porta e connessione e verificare che pure le richieste DNS siano inviate attraverso questa connessione sicura.
Aprire la pagina about:config e impostare il seguente booleano.
network.proxy.socks_remote_dns; default boolean true |
Se si vuole la possibilità di attivare e disattivare questa configurazione proxy con un click ci sono diversi add-on Firefox per la gestione delle configurazioni proxy come QuickProxy o FoxyProxy.
Popular Posts:
- None Found

++. I use it all the time!
Your a, an usage is wrong.
http://wordinfo.info/unit/3431/ip:1
Thanks Adam, i think that the original writer is German, I’ve corrected some a/an.
very useful info..
could you please tell in order to use this ssh setup as proxy , do i have to use static ip for my home pc or do i have to purchase a virtual privater server and use it as proxy.. or any other method for this..
Yes, you must have a static IP that you can reach via ssh.
So a computer at home with a static IP (or betetr an IP that you know), or a VPS are both good solutions.
You need to check out dynamic DNS services from dyndns or noip. They are free as long as you do not abuse them.
You can use Dynamic DNS service to avoid having to pay for a Static IP Address.
The most well known service is DynDNS: http://www.dyndns.com/
They offer a well written How-To: http://www.dyndns.com/support/kb/dyndns.html
Other services are available both free, and non-free, which may offer additional services:
http://dnslookup.me/dynamic-dns/
ciao linuxari, ottimo articolo (come sempre del resto).
volevo suggerire anche l’uso di tsocks per far confluire attraverso il proxy SOCKS anche il traffico dei software da riga di comando, così come descritto in un mio post sul mio blog.
Grazie per il commento e la dritta 😉
Vi ho conosciuto da poco e devo dire che siete fenomenali!
Ottimo articolo!
Consigliati!