Fool those who try to portscan your system!
The Portspoof program is designed to enhance OS security through emulation of legitimate service signatures on otherwise closed ports. It is meant to be a lightweight, fast, portable and secure addition to the any firewall system or security infrastructure.
The general goal of the program is to make the port scanning software (Nmap/Unicornscan/etc) process slow and output very difficult to interpret, thus making the attack reconnaissance phase a challenging and bothersome task
I’ve found the concept behind this small program really interesting : instead of close all your ports with a firewall deceive the real ports, thus annoying the guys who are running portscan versus your server/computer.
The Portspoof program primary goal is to enhance OS security through a set of techniques that will slow down and keep your attackers out from staying low profile during their reconnaissance against your system(s).
By default the attacker’s reconnaissance phase should be time consuming and easily detectable by your intrusion detection systems…
Art of Active (Offensive) Defense
Portspoof can be also used as an ‘Exploitation Framework Frontend’, that turns your system into responsive and aggressive machine. In practice this means that your server will be able to exploit your attackers’ tools and exploits in an automated manner. This approach is purely based on Active (Offensive) Defense concepts.
Features
- Fast : Multithreaded (by default 10 threads handle new incoming connections).
- Lightweight : Requires marginal amount of system resources.
- Portable : runs on Linux and on BSD (up to ver. 0.3)
- Flexible : You can easily use your firewall rules to define ports that are going to be spoofed.
- Effective against popular port scanners.
- Over 8000 false signatures that will fool port scanners!
- Open Source
Installation
Portspoof is a free software distributed under GNU GPL version 2 license, it’s not available as package in any repository, or at least for what I’ve (not) found around, so to install it you have to download the zip file from the official website, or clone the source repository from Github and follow these simple instructions:
1. Compile the software, go in the directory where you have unzipped/put the sources and give these commands:
$./configure $ make $ sudo make install |
OR
$ g++ -lpthread -Wall -g Configuration.cpp connection.cpp Portspoof.cpp revregex.cpp Utils.cpp Fuzzer.cpp Server.cpp -o portspoof |
2. Configure your firewall rules:
# iptables -A PREROUTING -i eth0 -p tcp -m tcp --dport 1:65535 -j REDIRECT --to-ports 4444 # iptables-restore < iptables-config (system_files directory) |
Note:
If you want to access your legitimate services you have to exclude their ports from the REDIRECT statement!
Portspoof by default will listen on port ALL_INTERFACES and port 4444 tcp. This FW rules will result in service obfuscation for port range from 1 to 65535
Run Portspoof with service emulation:
$ portspoof -c portspoof.conf -s portspoof_signatures -D |
Run Portspoof in “open port” mode:
$ portspoof -D |
3. Add portspoof to your system’s startup scripts.
To do this modify or use the default init.d script that you can found in the ‘system_files’ directory.
Demo
Do you want to test it, without any installation ?
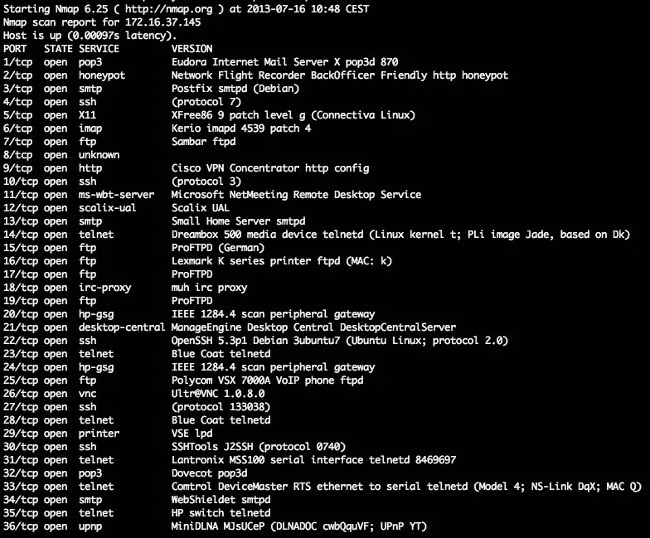
Check it out: Run your favorite port scanning tool for the address portspoof.org to see the results: nmap -sV -v portspoof.org
You should get something similar to this:
Reference:
Shall We Play A Game? Active Defense Against Port Scanning Authored by Piotr Duszynski
Popular Posts:
- None Found

Do you know for any other tools like this one?
Very interesting Tool!
How Can I to access my legitimate services for ex SSHD? Tanks
@giuseppe, you can white list your legitimate services in the nat table by simply using the ACCEPT target earlier than the REDIRECT rule. For example:
*nat
-A PREROUTING -p tcp -m multiport –dports 22,25,80,110,143,443,465,587,993,995,4190 -j ACCEPT
-A PREROUTING -p tcp -j REDIRECT –to-ports 4444
COMMIT
There is a package for ipfire gateway “portspoof-1.0-1.ipfire”
forum.ipfire.org/index.php?topic=9266.0
Hi,
I am a new Linux user with Ubuntu. I am trying to install portspoof. Its seemed to configure ok but when I use ‘make’, the message displayed. Can anyone help to find out the problem?
aw@aw-GA-MA770T-UD3:~/Downloads/portspoof-master$ make
Making all in src
make[1]: Entering directory `/home/aw/Downloads/portspoof-master/src’
make all-am
make[2]: Entering directory `/home/aw/Downloads/portspoof-master/src’
g++ -DHAVE_CONFIG_H -I. -DCONFDIR='”/usr/local/etc”‘ -g -O2 -MT portspoof-Revregex.o -MD -MP -MF .deps/portspoof-Revregex.Tpo -c -o portspoof-Revregex.o `test -f ‘Revregex.cpp’ || echo ‘./’`Revregex.cpp
Revregex.cpp:4:25: fatal error: openssl/aes.h: No such file or directory
#include
^
compilation terminated.
make[2]: *** [portspoof-Revregex.o] Error 1
make[2]: Leaving directory `/home/aw/Downloads/portspoof-master/src’
make[1]: *** [all] Error 2
make[1]: Leaving directory `/home/aw/Downloads/portspoof-master/src’
make: *** [all-recursive] Error 1
aw@aw-GA-MA770T-UD3:~/Downloads/portspoof-master$
This problem was already observed earlier:
https://github.com/drk1wi/portspoof/issues/12
but in my clone of portspoof I could not see the mentioned update either.
So I did it myself:
Just edit ~/portspoof/src/Revregex.cpp
and remove the two #include lines referring to openssl/aes.h and openssl/evp.h
.
Then compile again (sudo make install).
For me that solved the problem.
Regards
aqua