Steganography is the art and science of writing hidden messages in such a way that no one, apart from the sender and intended recipient, suspects the existence of the message, a form of security through obscurity. The word steganography is of Greek origin and means “concealed writing” from the Greek words steganos (στεγανός) meaning “covered or protected”, and graphei (γραφή) meaning “writing”. The first recorded use of the term was in 1499 by Johannes Trithemius in his Steganographia, a treatise on cryptography and steganography disguised as a book on magic. Generally, messages will appear to be something else: images, articles, shopping lists, or some other covertext and, classically, the hidden message may be in invisible ink between the visible lines of a private letter.
And now that we have saw the definition of this word, let’s take a look at three open source programs for Linux that you can use to play with this concept: Steghide and Outguess and one closed source Steg
Steghide
Steghide is a steganography program that is able to hide data in various kinds of image- and audio-files. The color- respectivly sample-frequencies are not changed thus making the embedding resistant against statistical tests.
Features:
- compression of embedded data
- encryption of embedded data
- embedding of a checksum to verify the integrity of the extracted data
- support for JPEG, BMP, WAV and AU files
The last release of this software it’s 10 years old, so it’s not exactly somethign new, but teh good news is that you should find it in the repositoy of any distribution, so install it with your package manager such as yum, apt or emerge.
Basic usage
Before starting make sure you have a suitable image for hiding information in it, and the information that you want to hide in a .txt file. In this example I have files called myimage.jpg and mysecret.txt in my home folder. After I’ve installed Steghide I can open a terminal and just type:
steghide embed -ef mysecret.txt -cf myimage.jpg |
This will prompt to enter a passphrase twice.
Or in the case that you don’t want to alter the original image you can use:
steghide embed -ef mysecret.txt -cf myimage.jpg -sf myNEWimage.jpg |
And to extract the information from the image you can use:
steghide extract -sf myimage.jpg |
This command will extract the txt file in the directory where you have run the program.
As a final step is important to note that the images or audio files can contain a determined maximum number of kb usable for hidden information and to find out how many kb has a certain image or audio file just give the command:
# steghide info myimage.jpg |
And you’ll get an output similar to this one:
# steghide info myimage.jpg "myimage.jpg": format: jpeg capacity: 3.5 KB Try to get information about embedded data? (y/n) |
Outguess
OutGuess is a universal steganographic tool that allows the insertion of hidden information into the redundant bits of data sources. The nature of the data source is irrelevant to the core of OutGuess. The program relies on data specific handlers that will extract redundant bits and write them back after modification. Currently only the PPM, PNM, and JPEG image formats are supported, although outguess could use any kind of data, as long as a handler were provided.
Outguess uses a generic iterator object to select which bits in the data should be modified. A seed can be used to modify the behavior of the iterator. It is embedded in the data along with the rest of the message. By altering the seed, outguess tries to find a sequence of bits that minimizes the number of changes in the data that have to be made.
Additionally, Outguess allows for the hiding of two distinct messages in the data, thus providing plausible deniablity. It keeps track of the bits that have been modified previously and locks them.
Basic usage
$ outguess -k "my_passwd" -d mysecret.txt myimage.jpg myoutput.jpg Reading input.jpg.... JPEG compression quality set to 75 Extracting usable bits: 43283 bits Correctable message size: 24627 bits, 56.90% Encoded 'hidden.txt': 1128 bits, 141 bytes Finding best embedding... 0: 587(50.6%)[52.0%], bias 68(0.12), saved: -2, total: 1.36% 15: 550(47.4%)[48.8%], bias 73(0.13), saved: 1, total: 1.27% 41: 585(50.4%)[51.9%], bias 32(0.05), saved: -2, total: 1.35% 198: 540(46.6%)[47.9%], bias 50(0.09), saved: 3, total: 1.25% 198, 590: Embedding data: 1128 in 43283 Bits embedded: 1160, changed: 540(46.6%)[47.9%], bias: 50, tot: 43059, skip: 41899 Foiling statistics: corrections: 174, failed: 187, offset: 158.255556 +- 316.069419 Total bits changed: 590 (change 540 + bias 50) Storing bitmap into data... Writing out.jpg.... |
Data Retrieval
You can retrieve data from an image in the following way:
$ outguess -k "my_passwd" -r myoutput.jpg mysecret.txt Reading out.jpg.... Extracting usable bits: 43283 bits Steg retrieve: seed: 198, len: 141 |
Steg
You want a software easier to use but that don’t let you know what’s doing exactly ?
Go for Steg a nice software also if closed source!
Steg is a cross-platform and portable software, written in C++. It use steganography and cryptography techniques to hide information inside uncompressed and compressed images. JPEG (JPG), TIFF, PNG, BMP image formats are supported. With it’s easy graphical user interface is possible to fine tune steganography parameters, evaluates image’s artifacts and uses both symmetric-key and asymmetric-key cryptography. Arbitrary data can be hidden as compressed archive file and it’s also possible to add a text comment.
Steg runs on GNU/Linux, Microsoft Windows and Apple Mac OS X, and you can download it directly from the official website.
Once installed you can start it and you’ll see something similar to this screenshot:
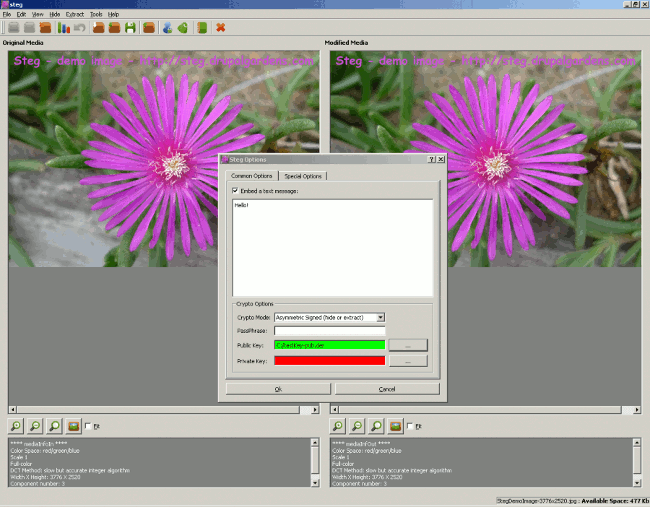
This screenshot show the Common tab of the Options dialog. Asymmetric Cryptography is selected. The green color mean that a valid public key was selected. The red color mean that the private key is invalid.
Having a graphical interface and the support of many more formats respect of previous programs makes this software much more user friendly than the others two, that only work on the command line.
Popular Posts:
- None Found
