Articolo di Dan Nanni pubblicato su xmodulo.com
Come amministratore di sistema Linux, tecnico di sicurezza o di controllo del sistema, la responsabilità può coinvolgere qualsiasi combinazione di questi: software per la gestione delle patch, scansione malware, controlli di integrità dei file, controllo di sicurezza, controllo degli errori di configurazione, ecc Se è presente uno strumento di analisi automatica delle vulnerabilità, si può risparmiare un sacco di tempo sul controllo dei problemi di sicurezza comuni.
Uno scanner di vulnerabilità per Linux è lynis . Questo strumento è supportato su più piattaforme tra cui CentOS, Debian, Fedora, FreeBSD, Mac OS e Ubuntu.
Per installare lynis su Linux, aprite un terminale ed eseguite i seguenti comandi:
$ wget http://www.rootkit.nl/files/lynis-1.3.0.tar.gz $ sudo tar xvfvz lynis-1.3.0.tar.gz -C /opt |
Per fare una scansione delle vulnerabilità Linux con lynis, eseguite i seguenti comandi.
$ cd /opt/lynis-1.3.0/ $ sudo /opt/lynis-1.3.0/lynis --check-all -Q |
Una volta che lynis iniziare a verificare il vostro sistema, svolgerà l’auditing in diverse categorie:
- Strumenti di sistema: binari di sistema
- Servizi al boot: boot loaders, servizi all’avvio
- Kernel: run level, moduli caricati, configurazione del kernel, core dumps
- Memoria e processi: processi zombie, processi in IO waiting
- Utenti, gruppi ed autenticazione: group IDs, sudoers, configurazione PAM, età delle password, default mask
- Shells
- File systems: mount points, file in /tmp, root file system
- Storage: usb-storage, firewire ohci
- NFS
- Software: Domini di ricerca DNS, BIND
- Porte e pacchetti : Pacchetti vulnerabili/aggiornabili, repository di sicurezza
- Networking: nameservers, interfacce in stato promiscuo, connessioni
- Stampanti e code di stampa: configurazione di cups
- Software: e-mail e messaging
- Software: firewalls: iptables, pf
- Software: webserver: Apache, nginx
- Supporto a SSH: Configurazione SSH
- Supporto SNMP
- Databases: MySQL root password
- Servizi LDAP
- Software: php: opzioni php
- Supporto Squid
- Registrazione dei log e files: syslog daemon, log directories
- Servizi insicuri: inetd
- Banners e identificazione
- Compiti programmati: crontab/cronjob, atd
- Accounting: sysstat data, auditd
- Time e sincronizzazione: ntp daemon
- Crittografia: Scadenza del certificato SSL
- Virtualizzazione
- Frameworks di sicurezza: Stato di AppArmor, SELinux, grsecurity
- Software: integrità dei file
- Software: malware scanners
- Home directories: shell history files
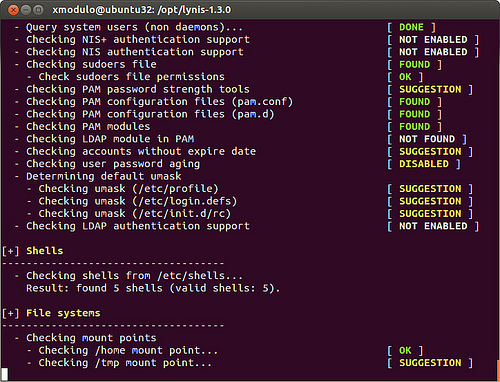
Uno screenshot di lynis in azione è mostrato qua sotto:
Una volta completata la scansione, la relazione sul del sistema viene generata e memorizzata in /var/log/lynis.log.
La relazione contiene avvertenze per potenziali vulnerabilità rilevate dallo strumento. Per esempio:
$ sudo grep Warning /var/log/lynis.log |
[20:20:04] Warning: Root can directly login via SSH [test:SSH-7412] [impact:M] [20:20:04] Warning: PHP option expose_php is possibly turned on, which can reveal useful information for attackers. [test:PHP-2372] [impact:M] [20:20:06] Warning: No running NTP daemon or available client found [test:TIME-3104] [impact:M]
The audit report also contains a number of suggestions that can help harden your Linux system. For example:
$ sudo grep Suggestion /var/log/lynis.log |
[20:19:41] Suggestion: Install a PAM module for password strength testing like pam_cracklib or pam_passwdqc [test:AUTH-9262] [20:19:41] Suggestion: When possible set expire dates for all password protected accounts [test:AUTH-9282] [20:19:41] Suggestion: Configure password aging limits to enforce password changing on a regular base [test:AUTH-9286] [20:19:41] Suggestion: Default umask in /etc/profile could be more strict like 027 [test:AUTH-9328] [20:19:42] Suggestion: Default umask in /etc/login.defs could be more strict like 027 [test:AUTH-9328] [20:19:42] Suggestion: Default umask in /etc/init.d/rc could be more strict like 027 [test:AUTH-9328] [20:19:42] Suggestion: To decrease the impact of a full /tmp file system, place /tmp on a separated partition [test:FILE-6310] [20:19:42] Suggestion: Disable drivers like USB storage when not used, to prevent unauthorized storage or data theft [test:STRG-1840] [20:19:42] Suggestion: Disable drivers like firewire storage when not used, to prevent unauthorized storage or data theft [test:STRG-1846] [20:20:03] Suggestion: Install package apt-show-versions for patch management purposes [test:PKGS-7394] . . . .
Allora, cosa state aspettando?
Una esecuzione può dare qualche buon suggerimento su come migliorare la sicurezza del sistema, ed una scansione regolare può aiutarci a vedere cambiamenti nel sistema ed a individuare malware.
Popular Posts:
- None Found

I tried to run it on Ubuntu 13.04 (beta). Got this error:
$ sudo /opt/lynis-1.3.0/lynis –check-all -Q
Fatal error: can’t find include directory
Make sure to execute Lynis from untarred directory or check installation
It’s in the Ubuntu archives already, just use apt-get install lynis. It’s far safer than just downloading a file over the net without cryptographic verification.
Copied and pasted your instructions. Execution comes back with
~$ sudo /opt/lynis-1.3.0/lynis –check-all -Q
Fatal error: can’t find include directory
Make sure to execute Lynis from untarred directory or check installation
Thanks for the feedback, it needs a cd :
~$ cd /opt/lynis-1.3.0/~$ sudo /opt/lynis-1.3.0/lynis --check-all -Q
Heya, great article. the commands given will never work however as you need to be in the directory before running. Just add a “cd /opt/lynis-1.3.0/” before running the command “sudo /opt/lynis-1.3.0/lynis –check-all -Q”
Thanks Liz,
I noticed this and posted an update in the same minute of your comment.
sounds like you should skip the step:
cd /opt/lynis-1.3.0/
Haven’t tried it yet, but that’s what it sounds like from
‘Fatal error: can’t find include directory
Make sure to execute Lynis from untarred directory or check installation’
In the first release of the article, the command
cdwas missing, this was the error.Now it’s fixed.
Thanks
yeah… posted while you were in the middle of fixing it, lol!
“Rico…. smoke bomb!”
Poooofffffff!!!!!!!!!!!!!!!!
Thank you.
Works fine after :
cd /opt/lynis-1.3.0/
Perhaps install from the Repo’s. I did (Kubuntu 13.04) and all went well.
both you guys need to run
/opt/lynis-1.3.0/lynis –check-all -Q
not
/opt/lynis-1.3.0/lynis –check-all -Q
debian doesn’t have sudo enabled by default, so I take it your running ubuntu so use sudo
Pretty epic, thank you very much for this. Do you think it is okay to use this on a web hosting server? Especially cPanel empowered servers?
Why not, you need a root account to do this but you’ll have a nice report and some useful things to check to start to check your security.
Amazing! I should get myself inspired using his scripts 😉
Worked like a charm the first run. lots of useful info. Thanks
To make it easier to view output I had added a simple menu to ease the output of logs under ubuntu.
hope this helps.
I ran it on Sabayon and worked flawlessly, thanks for the tip man.
changelog
* 1.3.0 (2011-12-25)
are you kidding? you recommend security tool that is no longer maintained?
I agree, and well done for at least CHECKING … How many people copied and pasted the instructions as root without even checking on the source!!
What’s the definition of being “maintained”? Every day a release?
The software is stable and even without updates for a year, that doesn’t mean the software is bad.
For readers who got scared after the remark above: new releases are available, it’s still maintained.
Inspired by script from AlanT, I made some changes in this script:
#!/bin/bash
#
# use $ sudo bash lynis.sh [quiet]
# where quiet does not produce detailed output
#
cd /opt/lynis-1.3.0/
if [ $1 = “quiet” ]
then
/opt/lynis-1.3.0/lynis –check-all -Q > /dev/null
else
/opt/lynis-1.3.0/lynis –check-all -Q
fi
echo
echo ” *** Check Warnings ***”
grep Warning /var/log/lynis.log
echo
echo ” *** Check Suggestions ***”
grep Suggestion /var/log/lynis.log
Great tool 😉
Be carrefully with this Suggestion :
[18:37:23] Performing test ID AUTH-9328 (Default umask values)
…
[18:37:23] Test: Checking /etc/init.d/rc
[18:37:23] Result: file /etc/init.d/rc exists
[18:37:23] Test: Checking UMASK value in /etc/init.d/rc
[18:37:23] Result: found umask 022, which could be improved
[18:37:23] Suggestion: Default umask in /etc/init.d/rc could be more strict like 027
If you modify this default umask given by rc to 027, dbus-daemon may become unaccessible to some daemons, like on these extracts of my syslog, and you ll lose access to graphical session 🙁
Tested for you on Debian-amd64
…
May 1 15:29:30 localhost bluetoothd[2422]: Bluetooth daemon 4.99
May 1 15:29:30 localhost bluetoothd[2422]: Unable to get on D-Bus
May 1 15:29:31 localhost avahi-daemon[2823]: Found user ‘avahi’ (UID 107) and group ‘avahi’ (GID 117).
May 1 15:29:31 localhost avahi-daemon[2823]: Successfully dropped root privileges.
May 1 15:29:31 localhost avahi-daemon[2823]: avahi-daemon 0.6.31 starting up.
May 1 15:29:31 localhost avahi-daemon[2823]: dbus_bus_get_private(): Failed to connect to socket /var/run/dbus/system_bus_socket: Permission denied
May 1 15:29:31 localhost avahi-daemon[2823]: WARNING: Failed to contact D-Bus daemon.
May 1 15:29:31 localhost avahi-daemon[2823]: avahi-daemon 0.6.31 exiting.
…
May 1 15:29:46 localhost gnome-session[3427]: libupower-glib-WARNING: Couldn’t connect to system bus: Failed to connect to socket /var/run/dbus/system_bus_socket: Permission non accordée
…
ay 1 15:29:46 localhost gnome-session[3427]: WARNING: Impossible de se connecter : Permission non accordée
…
May 1 15:30:21 localhost pulseaudio[4721]: [pulseaudio] core-util.c: Failed to connect to system bus: Failed to connect to socket /var/run/dbus/system_bus_socket: Permission non accordée
…
May 1 15:30:22 localhost pulseaudio[4790]: [pulseaudio] core-util.c: Failed to connect to system bus: Failed to connect to socket /var/run/dbus/system_bus_socket: Permission non accordée
May 1 15:30:22 localhost pulseaudio[4790]: [pulseaudio] module-console-kit.c: Unable to contact D-Bus system bus: org.freedesktop.DBus.Error.AccessDenied: Failed to connect to socket /var/run/dbus/system_bus_socket: Permission non accordée
May 1 15:30:22 localhost pulseaudio[4790]: [pulseaudio] module.c: Failed to load module “module-console-kit” (argument: “”): initialization failed.
May 1 15:30:22 localhost pulseaudio[4790]: [pulseaudio] main.c: Module load failed.
May 1 15:30:22 localhost pulseaudio[4790]: [pulseaudio] main.c: Échec lors de l’initialisation du démon
May 1 15:30:22 localhost pulseaudio[4772]: [pulseaudio] main.c: Échec lors du démarrage du démon.
May 1 15:30:22 localhost pulseaudio[5021]: [pulseaudio] core-util.c: Failed to connect to system bus: Failed to connect to socket /var/run/dbus/system_bus_socket: Permission non accordée
…
and so on
Otherwise, it’s a very nice and usefull audit tool!
for the same error, this solve my conf
$sudo vi /etc/group
../..
messagebus:x:106:avahi
../..
$sudo /etc/init.d/avahi-daemon restart
Excellent article.18 Suggestions and 4 Warnings! Now if I could only figure out how to implement them!
hello please is there any database for Lynis suppose if there how should i get it and how to store my Lynis log details into mysql database can anyone please help me thanks in advance