DDoS attacks (Distributed Denial-of-Service attacks) have been a global Internet phenomenon and a problem for quite some time now. Ever since the Internet started being used for making money and for generating large amounts of revenue, there have been people who have been trying (for whatever purpose) to bring down these webpages.
These attacks have a final goal of stopping the functioning of a website, which will, in turn, make it inaccessible for everyone on the Internet. Website downtime can, as I mentioned, bring about substantial losses of revenue, which is why these attacks have to be stopped at all costs.
Now, when it comes to the targets for these attacks, they are usually websites of some high-profile companies and businesses, as well as important government agencies. They target the websites that are hosted on major web hosting providers, ensuring that these pages stay down for a couple of hours.
If the problem is not dealt with, or is dealt with poorly, then the downtime can be prolonged indefinitely and can, after a while, cause the owner of the website (be it a business, a government agency or anything else) to break, usually financially.
Why is this important and why now?
The problem of the DDoS attacks has been present for quite some time, we can agree on that (after all, the first large reported DDoS attacks occurred on the University of Minnesota back in 1999).
So far, they have caused problems on the Internet, some of which have reached a great degree of seriousness. However, recently, the magnitude of the problem became too much to consider it something that will be dealt with on-the-go. An attack has been reported that has managed to threat the very foundations of what we know as the Internet today.
Namely, a Dutch web-hosting company has, reportedly, launched a never-before-seen attack on the spamhaus.org website and their DNS service, CloudFlare.
Firstly, the attack was launched on the website itself, causing Spamhaus to be cramped with packets of data (which amounted to about 10 Gbps) being sent their way.
Spamhaus is a website which is dedicated to fighting spam, blacklisting hosts and websites that have been proven to have spam activities on the web. Since this is done by volunteers, they have been referred to as the ‘vigilantes’ on the web. When they have blacklisted a hosting company called Cyberbunker, they have decided to retaliate by launching a DDoS attack against the website.
When people from Spamhaus saw that they cannot fend off the attack on their own, they contacted the Internet security company called CloudFlare and asked for their services. CloudFlare took charge and soon the attacks were redirected towards their servers. Had the size of data remained on the level of 10 Gbps, this would not have been a problem, but the attacks quickly increased in size and started fluctuating between 30 and 90 Gbps. Using their proven technologies, they were able to fend of these attacks as well, even though they continued to increase in size, reaching up to 120 Gbps.
When the attackers saw that they cannot achieve anything this way, they decided to alter their tactics and to try and cause more serious damage.
This time they decided to skip the website and to skip CloudFlare and instead went to attack the Tier 2 network providers which supplied CloudFlare. These relayed the attack to their suppliers, which are largely Tier 1 providers.
Since Tier 1 providers do not actually get connectivity from anyone, there was nowhere to relay the attack further. Instead, these providers had to suffer the full blow of the attack. If we take into consideration that these providers are what holds the Internet together, you can see how serious this is.
During March 23rd Internet users all over Europe experienced problems in accessing websites, and the guilt for this lies solely on this attack. Reportedly, but unofficially, the amount of data that flooded the Tier 1 providers exceeded 300 Gbps, which would mean that this was, by far, the largest DDoS attack ever seen, one which shook the very foundations of the Internet. Since they employed the DNS for their attack, the only way to immediately deal with the attack was to shut down this system, which would, in turn, shut down the Internet.
Now that we have understood what consequences a DDoS can have, we will move to explain more closely what it is.
Resources:
- http://staff.washington.edu/dittrich/misc/ddos/
- http://www.f5.com/glossary/distributed-denial-of-service-attack
- http://www.incapsula.com/ddos/ddos-attacks/botnet-ddos
- http://www.theverge.com/2013/1/28/3924248/ddos-how-a-tool-built-by-web-activists-became-the-ultimate-weapon-for
- http://thehackernews.com/2012/03/another-ddos-tool-from-anonymous-hoic.html
What is DDoS and what is its purpose?
A DDoS attack (short for ‘Distributed Denial-of-Service attack’) is an attack that has a goal to stop the functioning of a targeted website and to, as the name says, deny the services that it provides. There is a difference between a simple Denial-of-Service and a Distributed Denial-of-Service attack.
The difference is that, with the simple attack, only one computer is used to send large packets of data which will flood a server or a host of the targeted website, thus making it unreachable for ordinary users, because they will be unable to access it because of the large amount of data that has to be processed by the host.
A Distributed DoS utilizes several computers to do this, which makes it a more dangerous attack, because even larger amounts of data can be sent to flood the server, which usually results in greater downtimes. There is also a difference in defending against these two types of DoS attacks, but more on that later.
The purpose of these attacks is simple, as I said. Bring down the server which hosts the website, so that it would be unreachable for ordinary Internet users. However, this is not something that will be done to just any website. Almost always, the targeted websites are high-profile ones, which would suffer from loss of revenue due to the website downtime. The damage to the revenue can sometimes be measured in millions, which means that these attacks can be very effective.
What’s going on during a DDoS attack?
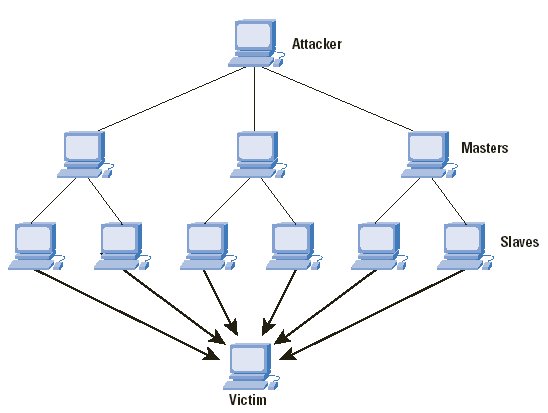
There are a few steps to every DDoS attack. As I explained, with the simple DoS attack, one computer is used to send packets of data to the targeted machine, until it overwhelms it with data, so that it becomes slow or completely shuts down. However, with a Distributed DoS, the process is a bit different. Here are the steps that every DDoS has.
The attacker finds one computer and makes it the DDoS master, the one to control all the others.
Using that master system, the attacker then starts communicating with other computer systems on the Web and tries to find a way to compromise their security and peruse them in the attack.
Utilizing tools that can be found on the Internet, the master system loads these tools onto other computer systems and makes them viable for abuse, making them, as we call it, zombie computers or bots. The more the zombies, the more severe the attack. There can sometimes be hundreds and thousands of these controlled machines. Every computer can be perused, basically, if left unprotected.
The final step is to have the master machine send a command to all the other zombie machines to start the attack by sending packets of data towards the targeted machine, all at once. These data packets do not have to be extremely large – the sheer number of controlled computers can sometimes do the trick, as there are a lot of requests being sent to the targeted machine at the same time.
Finally, after battling with such a large flow of data packets at the same time, the machine breaks down and becomes unavailable, thus denying service to the ordinary Internet users who wish to visit the targeted website.
As you may have guessed it, the owners of the zombie machines usually have no idea about their computer system being perused to do malicious things. This can be a big problem, because, as I said, any machine, if not properly protected, can be used to distribute the packets, without the owner knowing. This is why this is such a large threat to the security of the Internet itself.
What techniques can be utilized to fight DDoS?
As I stated above, there is a difference between fighting a DoS attack and a DDoS attack. The difference is simple. Because a DoS attack is carried from one machine only, this means that only one IP address is utilized to send the overwhelming packets of data. The solution is even simpler – find the IP address and block it.
However, with a distributed attack, the situation is more complicated. Since the attack is carried out from zombie machines or bots which have different IP addresses, simple blocking will definitely not do the trick. There are other ways that have to be utilized.
There are two types of fighting these attacks. One is to utilize the general techniques and the other is to utilize the filtering techniques.
General techniques are as follows:
- Unused services – disabling all the unused ports and applications on the machines;
- Security patches – installing all the relevant updates and security patches;
- IP broadcast – disabling the IP broadcast on the computer that is the host;
- Firewall – A firewall that is properly set can be the first line of defense against DDoS, however, with more complex attacks, it is a bit ineffective;
- IP hopping – changing the IP address of the website proactively, by choosing from a pool of predetermined addresses, which makes the website harder to target.
Filtering techniques, on the other hand, are as follows:
- SYN proxy – all the connection requests are screened and only those that are legitimate enough are let through.
- Aggressive aging – all the idle connections are removed from the connection tables, utilizing either firewalls or servers
- Blacklisting – all the potentially malicious IP addresses are sent to the blacklist, which means that they will not make connections
- Connection limiting – already established connections are always preferred, while new ones are rarely established
There are a few other tools for mitigating these attacks; however, these are the most important ones. Should you wish to find more, you can always search the Internet for solutions.
Are there services that can help me fight these attacks?
Because DDoS has grown from a small nuisance to such a large scale of attack (as I have written in the first paragraph), there have been a number of services established to help fight these attacks. I have already mentioned
CloudFlare as one of them. There are others, as well. They each utilize their own ways in which they fend off these attacks.
CloudFlare – they utilize a technology called ‘Anycast‘. What this system does is that it utilizes cloud servers to mitigate the attack by spreading the incoming data and connections to all the data centers that they have. This way, it is still possible for ordinary Internet users to access the website, because the data is evenly spread across the large number of servers.
Basically, this principle is directly opposite of what a Distributed DoS is. Fight large numbers with large numbers. Simple as that.
Cloudflare web performance & security
GlobalDots – on the other hand, GlobalDots utilize filtering techniques that I described in the last paragraph. Through filtering the unwanted IP addresses, it is easy to mitigate the attacks, because only users with validated IP addresses will be able to access the site, while zombie machines used for the attack will be blocked completely. They also use proxies to filter traffic and to direct it, when necessary.
Incapsula – they use a combination of the above two techniques. When dealing with a large volume attack, this service will utilize cloud defense and even out the attack. The good thing here, as well as with CloudFlare, is that the entire defense occurs off-network, meaning that only validated users will reach your website’s network. When the attacks are of a smaller scale, they utilize the filtering techniques described above, and some others, as well.
Conclusion
To sum everything up, I have to say that the DDoS attacks are currently threatening the entirety of the Internet, because, as we could see at the beginning of this article, even the Tier 1 providers (the core of the Internet) can be seriously harmed by these attacks.
Being that the point of the Internet is to be accessible at all times, I have to conclude that it is absolutely necessary to defend against this type of attacks. New technologies have to be found, but, for the time being, it is very advised to use the services that already exist, because they have proven to be really effective against such attacks.
Popular Posts:
- None Found


Great informations there, thanks for giving it.. DDoS are very difficult to prevent in much cases!