Guest post by Sophie Davidson
Modern day criminals are no longer entering banks with ski masks and pistols. Today’s felons are moving into cyberspace to accomplish their nefarious goals.
Remember the old adage, “a criminal always returns to the scene of the crime”? It turns out this maxim holds a lot of weight with regards to DDoS cybercrime.
Double DDoS
Recent research from BT revealed that about 41% of online businesses surveyed were victims of DDoS in the last 12 months. The more notable findings of the research showed that, of those attacked, over 78 percent were subsequently hit a second time shortly thereafter.
Distributed Denial of Service attacks or DDoS encompass a large variety of cyber threats designed to overwhelm a target’s server, or jam up their network. By disrupting a target’s resources, the hackers succeed in preventing normal traffic (such as users or customers) from passing through.
The effects of these attacks are potentially devastating. After being hit by a strong attack, it takes on average at least 12 hours to offer full service back to users.
What can happen in 12 hours? This sort of disruption could mean losing hundreds of thousands of dollars in revenue. Or, perhaps worse, the trust between the user and the online business, built up over months or years, could be lost in a matter of minutes.
Why Twice?
Imagine a thief who successfully stole out of a particular bank vault. Later he learns after the robbery that the bank has not changed their security infrastructure. He already knows the routes, the lock codes, the rotation of the guards—what’s stopping him from striking again?
This comparison describes the thought process and risk/reward assessment for a hacker. The big difference in the comparisons is that a DDoS offender is even more likely to strike again, simply because undefended sites are not likely to counter the second offensive. After all, unlike other hacking attacks, which are enabled by “security holes”, with DDoS there is no vulnerability to be patched and most defenders can’t scale up their network capacity to match the attackers’ offensive.
Also, DDoS offenders are less likely to be caught as the attack itself is executed indirectly, by hijacking other people’s computers
(a.k.a using DDoS botnets), which create a significant distance between the perpetrator and the target.
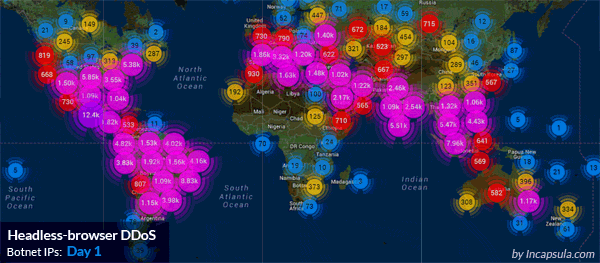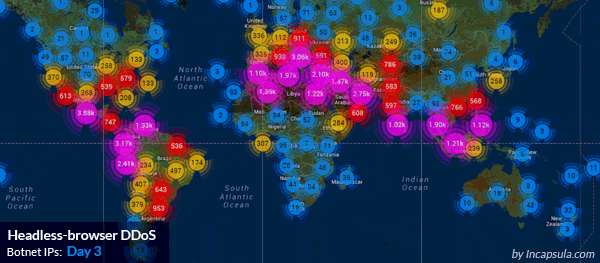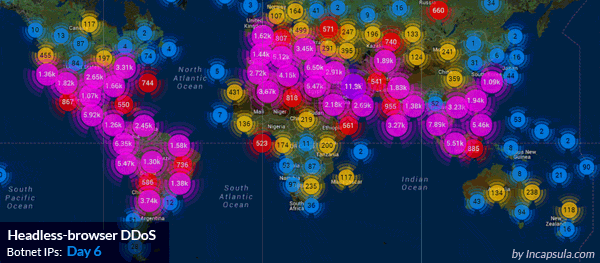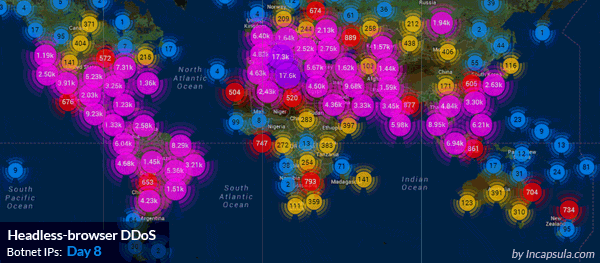
8 day-long DDoS attack, executed by 180,000 IPs worldwide. Source: Incapsula)
Only one out of ten of the security personnel interviewed in the BT survey said they strongly believed their institution or business was adequately prepared to defend against a future DDoS attack. This figure represents a shockingly large gap in security infrastructure for most online businesses.
But there are some companies that are prepared for online threats. Most of these businesses have DDoS protection from third party defense companies. Well-equipped security firms have the network capacity and security experience to stop DDoS attacks over 100 Gbps, or the equivalent of a data tsunami.
Preparing Your Online Business
Savvy business owners are gearing up for the oncoming DDoS escalation. Higher computing power plus the addition of more connected devices around the world have allowed hackers monstrous capabilities to carry out cyber attacks.
Loss of immediate and future sales, customer trust, and public relations fiascos—these are just a few of the consequences of being vulnerable to DDoS attacks. Make sure your website is ready for the first attack—and the second and the third.
Popular Posts:
- None Found