Article by Rahul Panwar first posted on http://linuxexplore.com/
A chroot on Unix operating systems is an operation that changes the apparent root directory for the current running process and its children. A program that is run in such a modified environment cannot name (and therefore normally not access) files outside the designated directory tree. The term “chroot” may refer to the chroot(2) system call or the chroot(8) wrapper program. The modified environment is called a “chroot jail”. From Wikipedia.
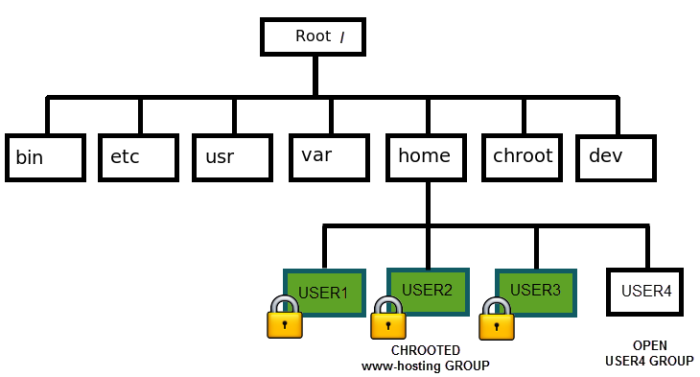
Why it is required? If you want to set up your Linux box as a web hosting server for its users, you may need to give SFTP access. But they can get access to whole system Linux tree, just for reading but still very unsecure. So it is mandatory to lock them in their home directory.
There are many other applications, it’s just a common example, so lets start its configuration.
Linux Box Detail:
Its mine Linux Box, your Linux system may vary. Only thing to take care is the openssh-server version, because openssh-server-5.3p1 support SFTP chroot. Older version supports but its tricky, please let me k now if you want to know that too.
Operating System: CentOS 6.3/x86_64
Kernel Version: 2.6.32-279.19.1.el6/x86_64
Openssh Server Version: openssh-server-5.3p1-81.el6_3/x86_64
sshd Server Configuration:
Add the following tail output to your Linux box’s SSH
server configuration file /etc/ssh/sshd_config.
[rahulpanwar@myhost ~]# tail -6 /etc/ssh/sshd_config #Subsystem sftp /usr/libexec/openssh/sftp-server Subsystem sftp internal-sftp Match Group www-hosting ChrootDirectory %h ForceCommand internal-sftp AllowTcpForwarding no
Then restart sshd service to enable this configuration.
[rahulpanwar@myhost ~]# sudo /etc/init.d/sshd restart
Create Chroot Users:
[rahulpanwar@myhost ~]# sudo mkdir /etc/skel/public_html [rahulpanwar@myhost ~]# sudo groupadd www-hosting [rahulpanwar@myhost ~]# sudo useradd -s /sbin/nologin -g www-hosting linuxexplore.com
Setting Permissions:
[rahulpanwar@myhost ~]# sudo chown root:www-hosting /home/linuxexplore.com [rahulpanwar@myhost ~]# sudo chmod 755 /home/linuxexplore.com
That’s all now create multiple users for web hosting, and offer the secure sftp access to your customers.
Shell Script to Create Web Hosting Users:
#!/bin/bash
HOSTING_DIR="/etc/skel/public_html"
CHROOT_GRP="www-hosting"
USR_NAME="$1"
[ ! -d "$HOSTING_DIR" ] && mkdir -p $HOSTING_DIR
grep ^"${CHROOT_GRP}:" /etc/group || /usr/sbin/groupadd www-hosting
grep ^"${USR_NAMEP}:" /etc/passwd || /usr/sbin/useradd -s /sbin/nologin -g $CHROO_GRP $USR_NAME
chown root:$CHROOT_GRP /home/$USR_NAME
chmod 755 /home/$USR_NAME
Selinux Configuration:
Disable the selinux permanently or configure it for read write user’s home directory in SSH chroot.
[rahulpanwar@myhost ~]# sudo setsebool -P ssh_chroot_rw_homedirs on [rahulpanwar@myhost ~]# sudo restorecon -R /home/$USERNAME
Troubleshooting
From: https://wiki.archlinux.org/index.php/SFTP-chroot
sshd[3505]: fatal: bad ownership or modes for chroot directory "/home/linuxexplore.com"
It’s ChrootDirectory ownership problem, sshd will reject sftp connections to accounts that are set to chroot into any directory that has ownership/permissions that sshd doesn’t consider secure. sshd’s apparently strict ownership/permissions requirements dictate that every directory in the chroot path must be owned by root and only writable for the owner. So, for example, if the chroot environment is in a user’s home directory both /home and /home/username must be owned by root and have permissions like 755 or 750 ( group ownership should allow user to access ).
If you are using sftp with public key check the following link:
http://www.centos.org/modules/newbb/viewtopic.php?topic_id=37903&forum=59
If chroot environment is in user’s home directory, make sure user have access to its home directory, or user would not be able to access its publickey, produce the error given in above CentOS forum link.
Popular Posts:
- None Found

In the shell script, I think that there is an error.
The variable
${USR_NAMEP}must be changed to${USR_NAME}, as declared.The articles is awesome, ignoring this typo.
Thanks.