Article By Chris Pentago
Goal of this how-to: Step to step guide on how to setup OpenDKIM with postfix on Debian GNU/Linux to send signed email from your VPS.
There are numerous methods or techniques that you can use to achieve email message signing. Good examples are DomainKey as well as DKIM which is an abbreviation for DomainKeys Identified Mail.
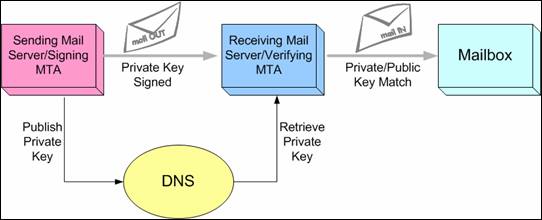
DomainKeys Identified Mail (DKIM) lets an organization take responsibility for a message that is in transit. The organization is a handler of the message, either as its originator or as an intermediary. Their reputation is the basis for evaluating whether to trust the message for further handling, such as delivery. Technically DKIM provides a method for validating a domain name identity that is associated with a message through cryptographic authentication.
These two techniques will not use symmetric encryption but rather will employ asymmetric encryption. (more info: http://support.microsoft.com/kb/246071) In both methods, the common algorithm used is RSA. This algorithm is also the default for these methods of achieving email message signing.
For those wondering about what asymmetric means, the following is a detailed explanation. It is a technique that utilizes a key to sign the email message. Other methods will not require a key. One can have two types of keys: a private key and a public key. These keys will come into play to verify the message as well. The two methods of creating email message signing as highlighted above are filters for SMTP server. DomainKey works with a dk-filter although this filter has been discontinued in the market. OpenDKIM has become the preferred replacement where filters are concerned.
A mail server must be enabled with a filter to set up the server properly. In light of this, Postfix can be used because it is enabled accordingly. Another requirement is the freedom to add or change the DNS records as you desire. With the above in mind, the following is a step by step guide on how to set up Postfix email server with DomainKey Indentified Mail on Debian.
1. The first thing is to update your software if you do not have Postfix installed already. Look at the manual provided to know exactly how to install the software. Once you have it running, move on to the next step.
On Debian, issue these commands:
aptitude update
aptitude safe-upgrade
2. At this point, it is important to install the DKIM filter. As hinted above, the most common and available filter is OpenDKIM. Installing this filter is not complicated at all and should not take much time.
aptitude install opendkim opendkim-tools
3. The next step involves setting up a directory for the storage of private keys. You can have as many domains as you wish but make sure that the permission settings are in order because they are the most critical.
mkdir -pv /etc/opendkim/example.com/
chown -Rv opendkim:opendkim /etc/opendkim
chmod go-rwx /etc/opendkim/*
4. Here, security is pivotal and it will warrant you to create a key pair for each domain you have. In other words, every single domain should have a key pair and this is the way to go.
cd /etc/opendkim/example.com/
opendkim-genkey -r -h rsa-sha256 -d example.com -s mail
mv -v mail.private mail
chown opendkim:opendkim *
chmod u=rw,go-rwx *
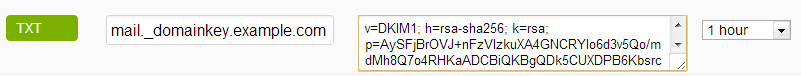
5. The next thing to do is to publish a public key using the DNS record. You will be required to insert new TXT DNS record with key generated previously. You’ll be presented with key in Bind (DNS Server) format but it’s easy to paste necesary parts to your domain’s DNS provider:
mail._domainkey.example.com IN TXT "v=DKIM1; h=rsa-sha256; k=rsa;p=AySFjB......xorQAB"
Example on how it look in CloudFlare’s DNS manager:
6. At this juncture, it is vital to set up the key table. You will do this by using a specified format:
KeyID Domain:Selector:PathToPrivateKey
So fire up your text editor of choice and open/create /etc/opendkim/KeyTable file our example looks like this:
example.com example.com:mail:/etc/opendkim/example.com/mail
7. The next step involves setting up the signing table. The filter used is programmed to read the table by looking for matched domain. Again, open/create /etc/opendkim/SigningTable in your favorite text editor and put this into it:
*@example.com example.com
8. You will then have to create a /etc/opendkim/TrustedHosts file at this point. It will list the top trusted hosts as you desire. Again, the format used can be as given earlier when creating a signing table as well as a key table.
127.0.0.1
lola.ns.cloudflare.com (this is DNS server you'll get from your provider)
example.com
9. Next, set up the ownership of files we just created:
chown opendkim:opendkim /etc/opendkim/KeyTable
chown opendkim:opendkim /etc/opendkim/SigningTable
chown opendkim:opendkim /etc/opendkim/TrustedHosts
10. This step is critical because it involves configuring the OpenDKIM filter to read the files that you have created above. Do this by opening /etc/opendkim.conf using your chosen editor. Consequently, it might be good to delete the Debian configuration so that you can replace it with the new and edited information.
# Enable Logging
Syslog yes
SyslogSuccess yes
LogWhy yes
# User mask
UMask 002
# Always oversign From (sign using actual From and a null From to prevent malicious signatures header fields (From and/or others) between the signer and the verifier)
OversignHeaders From
# Our KeyTable and SigningTable
KeyTable refile:/etc/opendkim/KeyTable
SigningTable refile:/etc/opendkim/SigningTable
# Trusted Hosts
ExternalIgnoreList /etc/opendkim/TrustedHosts
InternalHosts /etc/opendkim/TrustedHosts
# Hashing Algorithm
SignatureAlgorithm rsa-sha256
# Auto restart when the failure occurs. CAUTION: This may cause a tight fork loops
AutoRestart Yes
# Set the user and group to opendkim user
UserID opendkim:opendkim
# Specify the working socket
Socket inet:8891@localhost
11. It is now time to change or configure the OpenDKIM filter on Postfix. This can be done by simply altering some parameters to achieve what you require. It is very important to do this carefully so that you avoid any errors that may come up later. Open /etc/postfix/main.cf and add/uncomment these lines:
# OpenDKIM
milter_default_action = accept
milter_protocol = 2
smtpd_milters = inet:localhost:8891
non_smtpd_milters = $smtpd_milters
12. When you reach this step, you are almost there. You will however be required to restart OpenDKIM service as well as Postfix. After doing this, make sure that everything is fine for you to move on to the final step.
service opendkim start
13. The final step is to check whether the changes you were making have turned out well. Check if OpenDKIM service is online and listens on port we defined above.
ps aux | grep dkim
netstat -tanp | grep dkim
This method works like a charm and it is the sure way to attain email messaging signing. It is really not a complicated process but you will need to follow the method to the letter. Beyond the technical jargon, any person willing to follow this guide diligently can achieve success. Keep in mind that the top benefits of DKIM is to curb abuse as well as to reduce spamming to recipients.
It is a method to verify how genuine an organization or a domain is. There are many other elements that will play a good role in helping your business or domain establish a credible name in the market through this process.
This is especially important if you plan to send email from your server outside to GMail or Hotmail servers with increased security/spam filters or your mail may end up sent to SPAM folder or even rejected.
If you followed the procedure but still unable to send mail to GMail for instance, ask your web host to set you up with ReverseDNS so those mail receiving servers could match message header IP address with your domain.
If your VPS or dedicated server are located in highly available and secure government data centre such as Macquarie’s or TheBunker’s, these indetifying features might be already set by default for their new customers.
Popular Posts:
- None Found

Interesting article. Thanks!
Does this also work for vitual domains? Perhaps you might do another howto for using OpenDKIM with virtual domains.
Of course it works, one just needs to create separate setting for each of his domains. Check step 3. 🙂
You could perhaps modify the schema : publish/retrieve the public key (and not the private key)
Why did you set milter protocol 2, not 6?
at first: thank you very much for your tutorial, but i found one thing not working as expected when sending emails to this test service:
http://www.brandonchecketts.com/emailtest.php
it tells mit that “public key: does not support hash algorithm ‘sha256′”, so i recreated the keys with the following option removed: “-h rsa-sha256”
No everything works like a charm.
Hello Florian,
Thanks a lot for the feedback and the useful information.
Thank you very much for your helpful tutorial.
I had an issue with opendkim failing to find the key, throwing an error like this:
signing table references unknown key 'example.com'I was able to solve this problem by modifying the entry for KeyTable in the opendkim configuration file (shown in step 10 above). Removing the “refile:” portion of the KeyTable line did the trick:
KeyTable /etc/opendkim/KeyTable(Note that the SigningTable entry should still use “refile:”.)
For reference, I am using opendkim 2.6.8. Perhaps the format for the configuration file has changed between versions.
The “-h” parameter should be only “sha256” and not “rsa-sha256”.
From the reference RFC: http://tools.ietf.org/html/rfc6376#page-27
key-h-tag = %x68 [FWS] "=" [FWS] key-h-tag-alg
*( [FWS] ":" [FWS] key-h-tag-alg )
key-h-tag-alg = "sha1" / "sha256" / x-key-h-tag-alg
x-key-h-tag-alg = hyphenated-word ; for future extension
Help me out whenever I need to freshly set up my server! You should consier accepting tips via Bitcoin. 😉
Thank so much, this article is very helpful, but i found error in “OversignHeaders From” on step 10, i don’t know how to fix this. please help me.
Nice guide but it needs an update
opendkim-genkey -r -h rsa-sha256 -d example.com -s mailshould beopendkim-genkey -r -h sha256 -d example.com -s mailelse it generates a permerror testing dkim at elandsys auto test
sorry missed it was already told
steel alive?
at today I’m looking for solution to error “unknown hash ‘rsa-sha256′” when testing my record key on my dns, i’m testing and looking to fix and no solution, i had generated the key by some ways with or without the -h sha256, -h SHA256 parameters and updated the record file them testing and receive the same error “unknown hash ‘rsa-sha256’